Information Governance
Protect your sensitive data and mitigate security risks.
The volume of data that businesses generate today is not only unprecedented but also continuing to grow dramatically at a rate. The Big Data Era has created a perfect storm for companies—litigation costs have skyrocketed, storage concerns are omnipresent, and information security threats have never been greater. TransPerfect Legal helps clients navigate their regulatory and technical landscape, and reduce risk.
Information Security and Defensible Dat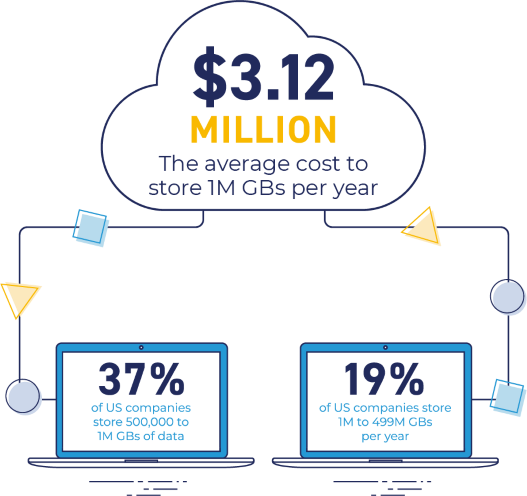 a
a
Data storage is not only expensive, but also a key driver of privacy and cyber security risks. For a typical company, 70% of data stored has no operational or legal value.
As one of the leading information security service providers, TransPerfect Legal identifies the data that you actually need to preserve and customizes your defensible data disposition plans according to your company’s operations, regulatory environment, and resources. Our certified digital forensics experts help alleviate your big data pain points by mitigating the challenges associated with e-discovery, privacy, and information security.
We monitor information compliance and cyber threats through security assessments, breach response planning, review of vendor contracts, and internal training to educate your employees on corporate policies.
Governance, Risk, and Compliance
Securely access, search, and manage your data with 50% greater efficiency.
TransPerfect Introspec is a GRC management platform used by legal, privacy, and compliance professionals to significantly streamline their data governance. We provide a wide range of information security risk assessments to provide your business with the ultimate safety and information security, including:
- Audit and Design of Corporate Policies and Procedures
- Security Incident Investigation
- Incident Response Plan Design and Tabletop Exercises
- Review of Vendor Contracts
- Data Mapping, PII, and CJA
- Employee Education Training
- Continuity and Recovery Planning

Risk Assessment
Decrease Litigation Costs - In a typical dispute, e-discovery costs make up 60–70% of total legal spend. We shrink your data profile, immediately decreasing litigation costs.
Mitigate Cyber Exposure - With our information security assessment, we learn your data to enforce a more secure profile, making sure you realize where your company’s sensitive and personal data resides.
Save Money on Data Storage - By eliminating digital debris, TransPerfect provides you savings on direct and indirect costs associated with storing and maintaining huge troves of data.
Remain Compliant - Federal, state, and local regulations overlap with sector-specific standards. TransPerfect Legal understands the complex web of regulatory obligations and builds your intelligent, straightforward retention policy.
Data Privacy
Your employees, customers, and business partners need to know how their sensitive and personal information is being collected, used, and protected. The TransPerfect Legal data privacy and consulting group ensures your policies and privacy settings are consistent with each other and with your business requirements. With our precise and detailed information security risk assessments, sensitive data is protected across your technological landscape.
Data Protection for Employee Departures
Identification, Imaging, and Preservation - Create forensic preservation images of computers, devices, and all other data repositories accessible to departing employees.
Preliminary Forensic Analysis and Reporting - Identify “red flags” in computer access logs, time stamps, USB history, internet history, lists of deleted files, and trash bins.
Comprehensive Forensic Analysis and Reporting - Investigate flagged cases that show potential theft and report all breaches including sensitive data.
Expert Consulting and Litigation Testimony - Protect against data breaches by customizing technical and administrative controls, and support data misappropriation cases with expert testimony.
Data Remediation and Hardware Wiping - Remediate misappropriated data from a competitor’s infrastructure and internally recycle hardware immediately following forensic preservation.


